19.1.2.WebDAV Authentication
Virtuoso WebDAV offers two types of authentication dependent on the connecting clients abilities. These are:
| Basic (Clear Text) Authentication - sends passwords over the connection in clear text. Clear text passwords can be intercepted and read so should be avoided or used only if you encrypt passwords through SSL. |
| Digest Authentication - passwords are always transmitted in an MD5 hash. |
Basic Authentication
Basic Authentication is a widely used, industry-standard method for collecting user name and password information. The following steps outline how a client is authenticated using Basic authentication:
-
The client browser displays a dialog box for a user to enter a user name and password (his/her credentials).
-
The client browser then attempts to establish a connection to the server using the user's credentials. The clear text password is Base64-encoded before it is sent over the network.
-
If a user's credentials are rejected, the client may re-display the authentication dialog box to re-enter the user's credentials. Failing to supply correct details will terminate the connection, reporting an error to the user.
-
When Virtuoso verifies that the user name and password are valid, a connection is established.
The advantage of Basic authentication is that most clients support it. The disadvantage is that it transmits passwords in an unencrypted form. Simple network monitoring can easily reveal your password. Basic authentication is not recommended unless you are confident that the connection between the user and Virtuoso is secure.
![[Note]](images/note.png) |
Note: |
|---|---|
|
Base64 encoding is not encryption. A Base64-encoded password can be easily intercepted by a network sniffer and easily decoded. |
Digest Authentication
Digest authentication provides a security improvement over Basic authentication in how a user's credentials are sent across the network. Digest authentication transmits credentials across the network as an MD5 hash, or message digest, where the original username and password cannot be deciphered from the hash. Digest authentication relies on the HTTP 1.1 protocol as defined in RFC 2617, which not all browsers support.
The following steps outline how a client is authenticated using Digest authentication:
Figure19.1.Digest Authentication
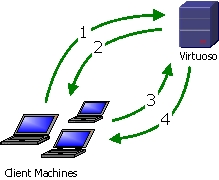
-
The client requests a file or connection from Virtuoso.
-
Virtuoso challenges the request, informing that client: Digest is in use, what the realm name is.
-
The client prompts the user for credentials. The client creates an MD5 hash of the credentials and the realm name and resubmits the request, this time supplying the MD5 hash.
-
If Virtuoso approves the credentials then the resource or connection is granted to the client, and the data is returned.